-
 Sebastian Toader |
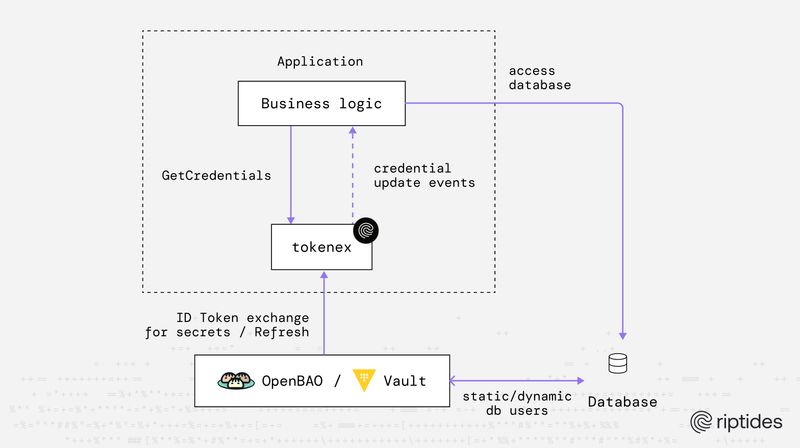
Sebastian Toader |tokenex adds Vault & OpenBao support: Exchanging ID tokens (JWTs) for secrets without static credentials
Vault and OpenBao become first-class citizens in tokenex’s identity-driven workflow, unifying access to cloud credentials and application secrets, without static Vault tokens, long-lived credentials, or manual secret distribution through the same identity-based access pattern.Credentials -
 Sebastian Toader |
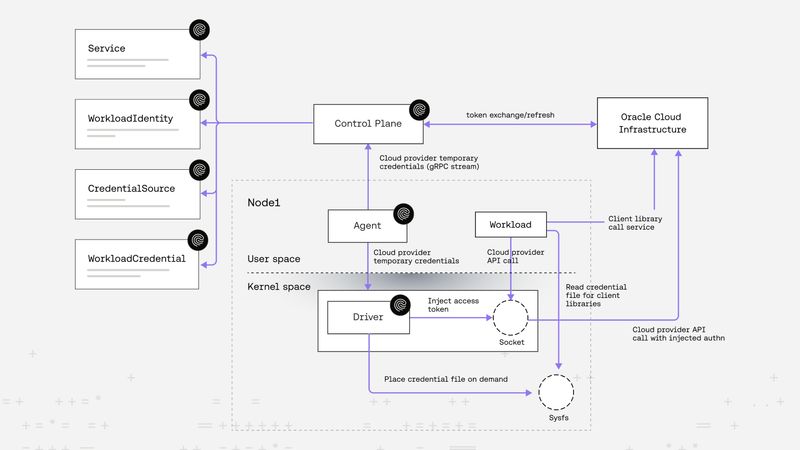
Sebastian Toader |Secretless OCI Authentication with SPIFFE-based workload identity
Riptides brings secretless, on-the-wire credential injection to non-human clients. Instead of storing long-lived credentials, workloads receive short-lived credentials dynamically and transparently at runtime, they are injected and automatically refreshed. In this post, we demonstrate the approach using OCI's CLI — but the same pattern applies across any cloud or service provider, reducing risk and simplifying non-human identity management.Federation -
 Marton Sereg |
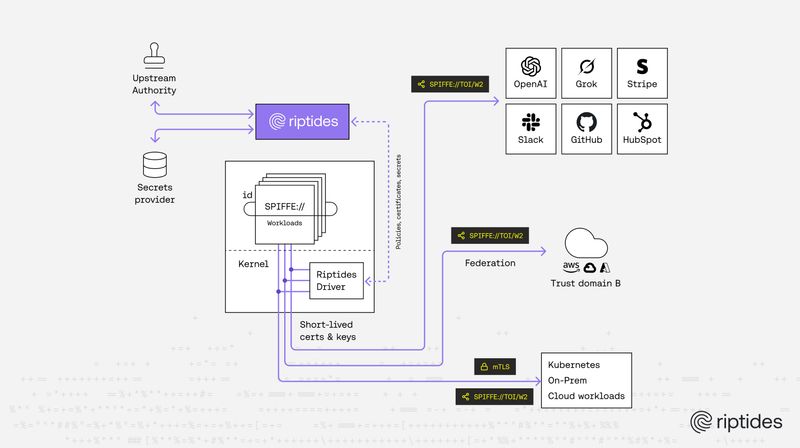
Marton Sereg |When Remote Code Execution Isn’t the End — Designing for Containment
Remote Code Execution is inevitable in complex systems — what matters is whether it leads to lateral movement. By enforcing identity at the process level and securing internal communication with mutual TLS, RCE becomes a contained event instead of a cascading breach.Security -
 Balint Molnar |
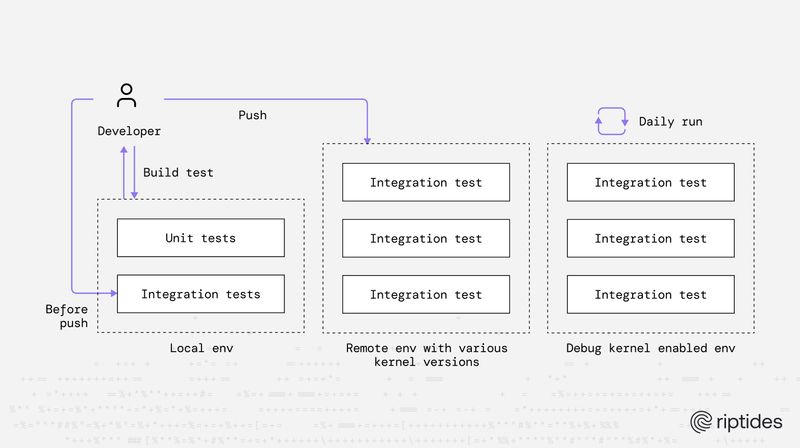
Balint Molnar |Testing Linux Kernel Modules with Bats
Riptides tests kernel-level code the same way we build it: with precision and discipline. This post walks through our multi-layer testing pipeline, from isolated unit tests to Bats driven integration suites and daily runs on instrumented debug kernels. We show how we validate behaviour across distributions, enforce metric correctness, and use real shell-based workflows.Testing -
 Sebastian Toader |
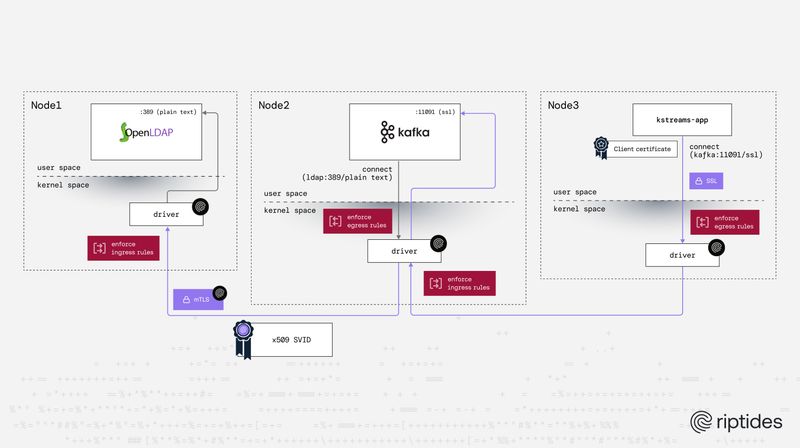
Sebastian Toader |Supercharge Kafka security with Riptides
Riptides brings identity-first, zero-trust security to Kafka with no application changes, eliminating secrets, automating mTLS, and removing the operational burden of managing keystores and truststores. It transparently upgrades plaintext to authenticated encryption, dramatically strengthening Kafka’s security posture.Security -
 Nandor Kracser |
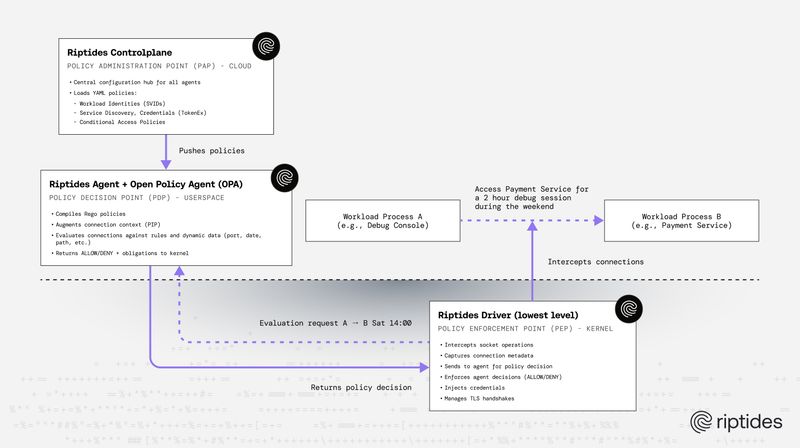
Nandor Kracser |Introducing Riptides Conditional Access: Fine-Grained, Time-Aware Security Policies
Riptides Conditional Access extends workload identity with time-based, HTTP-aware, and usage-based policoes. Our XACML-inspired model and OPA evaluation let you enforce real zero-trust decisions between microservices, from limiting database access to business hours, to enforcing read-only API paths, to much more fine-grained behavior.Security -
 Janos Matyas |
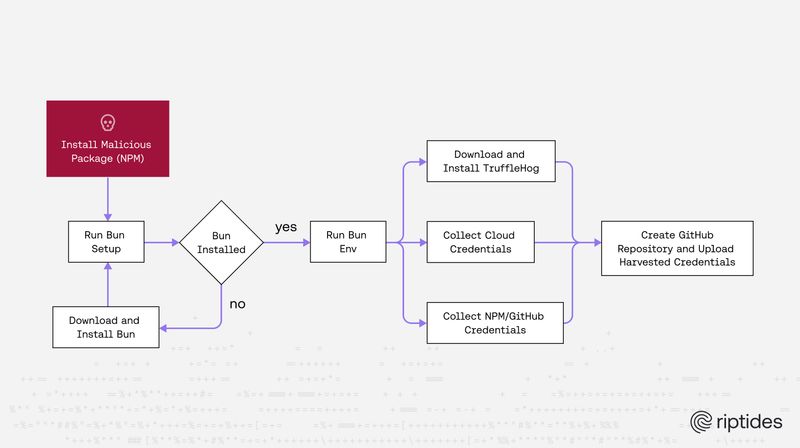
Janos Matyas |Shai-Hulud 2.0: A Technical Breakdown and Why Secrets Need to Die
Shai-Hulud 2.0 showed how easily long-lived tokens and static secrets can be harvested and weaponized to hijack supply chains at scale (again). One of the meaningful fixes is shifting to identity-based, ephemeral, SPIFFE-driven authentication, an approach Riptides strongly advocates for and builds upon.Security -
 Peter Balogh |
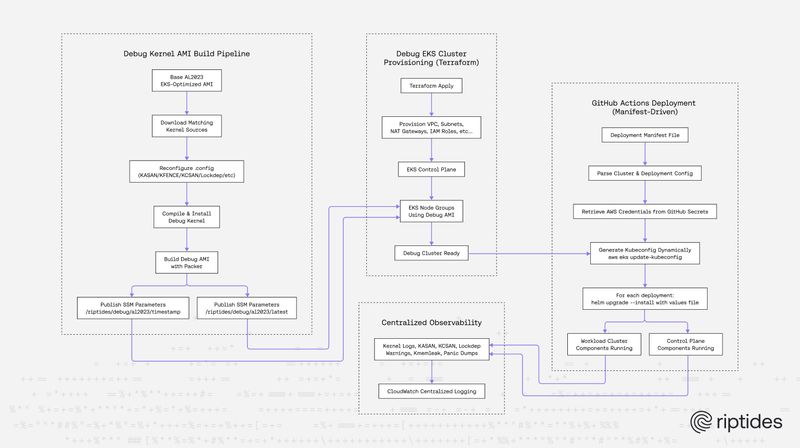
Peter Balogh |From Build to Root Cause: How Riptides Debugs Its Kernel Module in Real Clusters
At Riptides, SPIFFE-based identities and encrypted communication start in the kernel. When your trust fabric lives that deep, fast builds and full test coverage aren't optional, they're essential. In this post, we show how we built a scalable, automated debugging pipeline using EKS, custom debug kernels, and EC2 runners to catch the tricky kernel bugs that only appear under real workloads.Kernel -
 Zsolt Rappi |
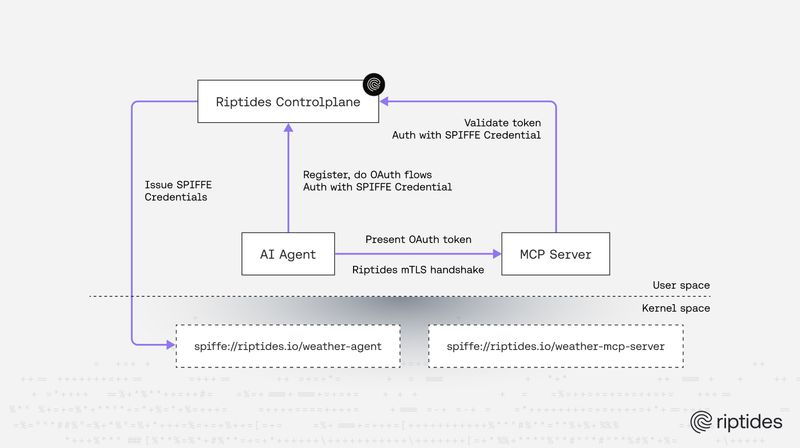
Zsolt Rappi |Bringing SPIFFE to OAuth for MCP: Secure Identity for Agentic Workloads
Built on emerging OAuth RFC drafts and using SPIFFE based identities, workloads in an MCP environment can authenticate and obtain tokens without client secrets. This approach enables self-registering, verifiable, and fully automated trust across agentic AI systems.SPIFFE -
 Sebastian Toader |
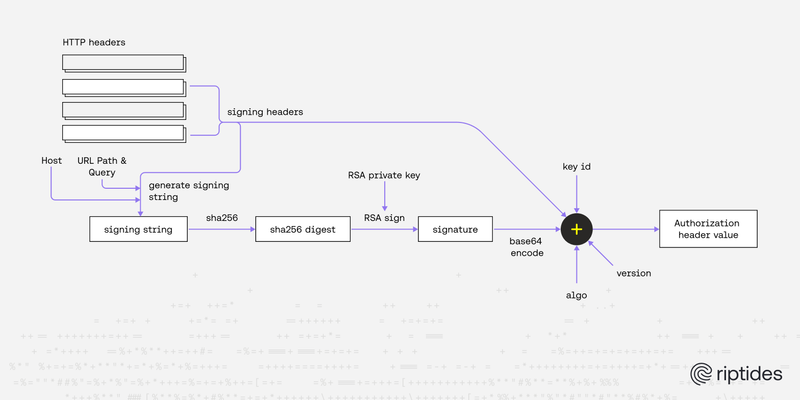
Sebastian Toader |Announcing oci-req-signer-c: A Lightweight C Library for Oracle Cloud Request Signing
We’ve released oci-req-signer-c, a lightweight and portable C implementation of Oracle Cloud request signatures, built for kernel-based and embedded environments. It requires zero allocations, supports pluggable crypto backends, and depends on minimal system headers. Designed to integrate seamlessly with your own HTTP parsing, it’s an ideal fit for constrained platforms that need to communicate securely with Oracle Cloud.Kernel -
 Marton Sereg |
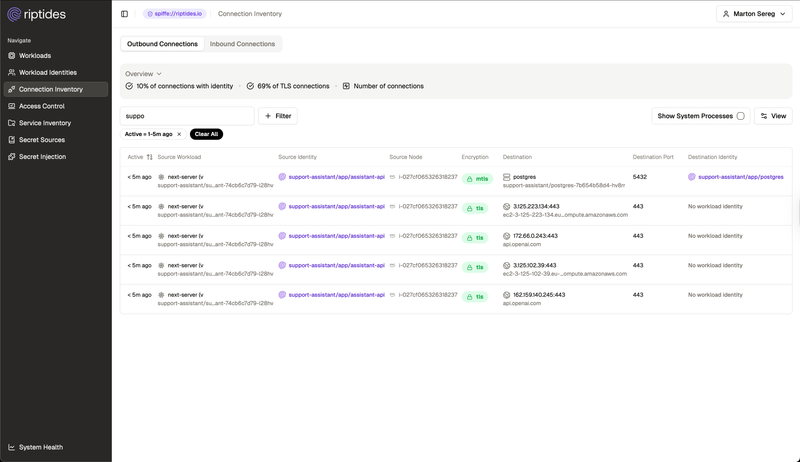
Marton Sereg |Growing Threat of npm Supply Chain Attacks and the Runtime Fix That Stops It
Open-source dependency chains make development fast, but npm supply-chain compromises can turn a single install into a full cloud breach. Just-in-time secret injection tied to workload identity removes persistent targets for scrapers, dramatically reducing the blast radius while keeping applications running without code changes.Identity -
 Balint Molnar |
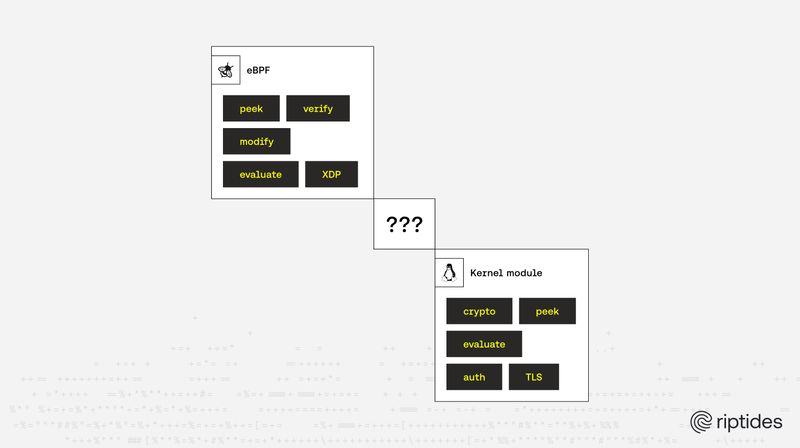
Balint Molnar |When eBPF Isn’t Enough: Why We Went with a Kernel Module
Riptides chose a kernel module over eBPF for secure workload identity and credential management. While eBPF offers excellent observability and network control, its limitations in cryptography and system integration make it unsuitable for deep security operations. We outline Riptides’ reasoning and demonstrate why kernel modules remain essential for transparent, high-assurance identity and TLS management within the Linux kernel.Security -
 Janos Matyas |
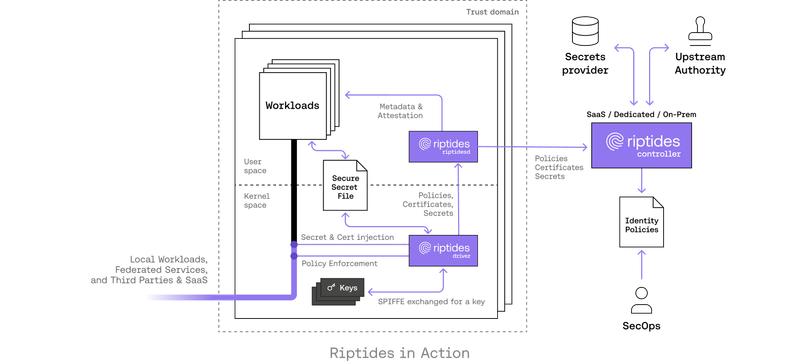
Janos Matyas |Why Riptides Embraces SPIFFE But Not SPIRE
The SPIFFE standard provides the foundation we rely on for non-human workload identity, but we’ve extended it beyond user-space implementations like SPIRE, offering transparent certificate management, real-time policy enforcement, deep observability, and seamless, end-to-end encrypted communication directly from the kernel.Kernel -
 Peter Balogh |
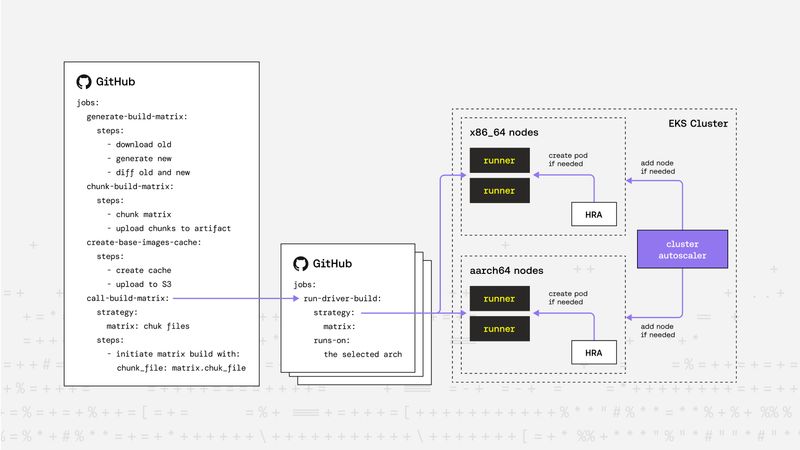
Peter Balogh |Beyond the Limits: Scaling Our Kernel Module Build Pipeline Even Further
For Riptides, secure SPIFFE-based workload identities and encrypted communication begin in the kernel. When your trust fabric runs that deep, build speed and coverage become mission-critical. This post shows how we scaled our kernel module builds beyond GitHub Actions’ native limits using matrix chunking and custom base images.Kernel -
 Zsolt Varga |
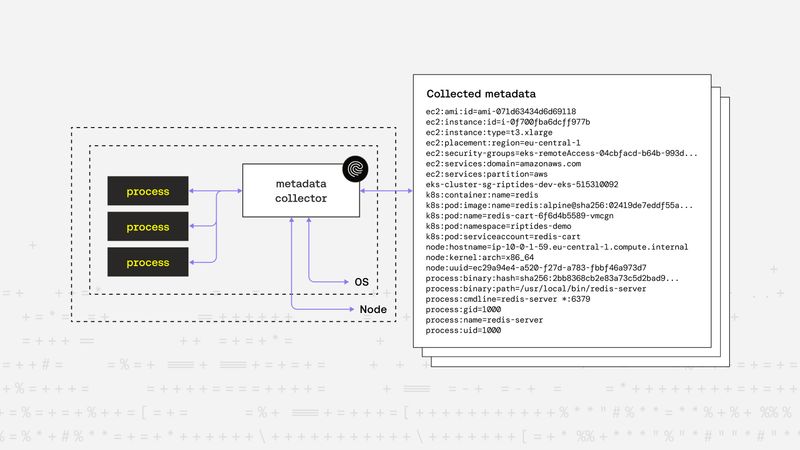
Zsolt Varga |Workload Attestation and Metadata Gathering: Building Trust from the Ground Up
Every SPIFFE ID, certificate, and mTLS handshake at Riptides originates in the Linux kernel and begins with a single question: can we prove who this workload really is? This post explores how process-level evidence becomes the foundation of verifiable trust across the system.Kernel -
 Janos Matyas |
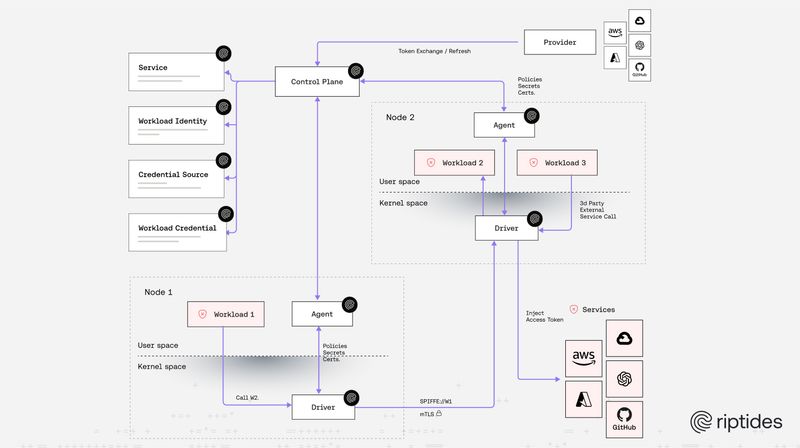
Janos Matyas |Zero Trust: From Perimeter to Kernel — How Riptides Pushes the Boundary
Most zero trust ends at the perimeter; ours begins at the kernel. Riptides brings attestation, cryptographic SPIFFE-based identity, and policy enforcement directly from the Linux kernel, eliminating implicit trust from the inside out. We verify workloads, not just connections, enforcing identity and policy the moment they come alive.Vision -
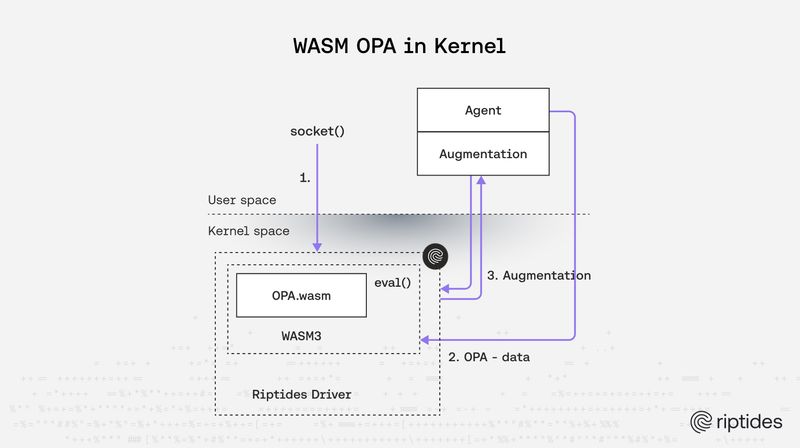 Nandor Kracser |
Nandor Kracser |From Kernel WASM to User-Space Policy Evaluation: Lessons Learned at Riptides
At Riptides, we issue identities directly to workloads in the kernel and use OPA policies to secure and orchestrate their communication. These policies govern socket connections in real time, allowing us to enforce fine-grained, identity-aware decisions at the moment workloads talk to each other. We pioneered running OPA-compiled WASM in the kernel itself — a novel but unsustainable approach that we ultimately replaced with a more pragmatic user-space design.Kernel -
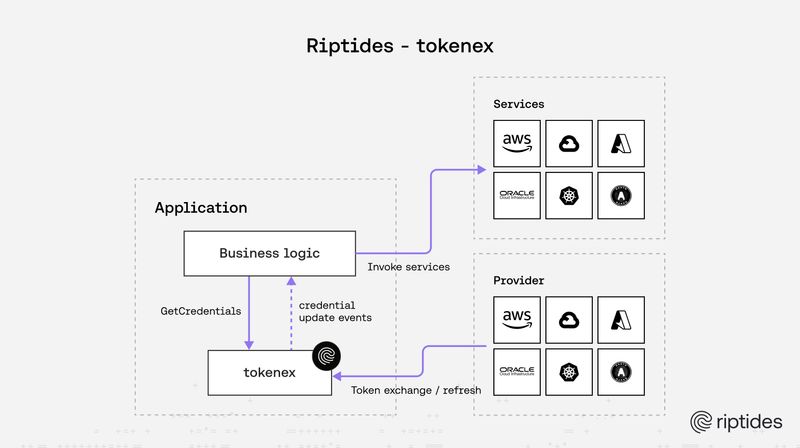 Sebastian Toader |
Sebastian Toader |Introducing tokenex: an open source Go library for fetching and refreshing credentials
Managing short-lived cloud credentials across AWS, GCP, Azure, and OCI is messy. Every provider has its own exchange flow, refresh logic, and config sprawl. We built [tokenex](https://github.com/riptideslabs/tokenex) — an open source Go library that gives you a single, consistent API to fetch & refresh short-lived credentials across clouds.Credentials -
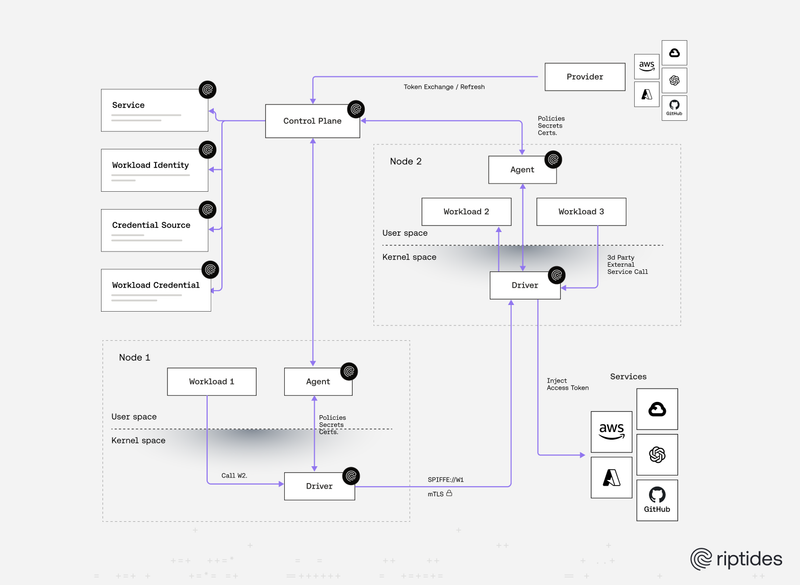 Janos Matyas |
Janos Matyas |Workload Identity Without Secrets: a Blueprint for the Post-Credential Era
Static secrets are a liability and credentials are breached every day. With SPIFFE as the foundation, workload identity without stored secrets delivers cryptographic, ephemeral trust for the post-credential era. Riptides takes this further with kernel-native enforcement, making identity automatic, process-bound, and truly seamless.Kernel -
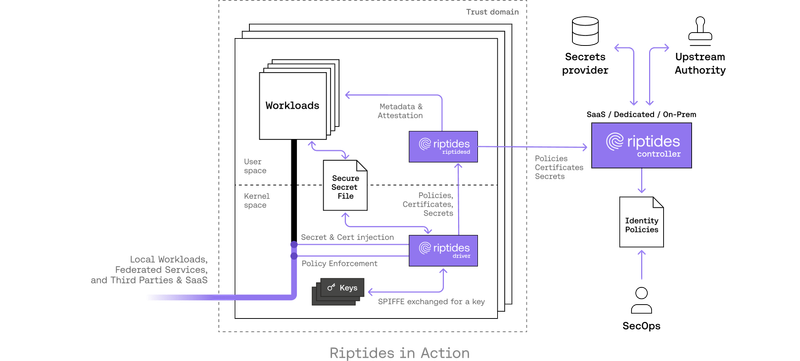 Janos Matyas |
Janos Matyas |Shai-Hulud and the Secret Hunters: How npm Installs Turn into Intrusions
Static secrets are a supply-chain’s Achilles’ heel. Shai-Halud exploits this by harvesting and validating tokens from repos, CI, and developer machines; Riptides turns the tables by moving identity off disk and injecting credentials on-the-wire, making stolen files useless.Security -
 Zsolt Varga |
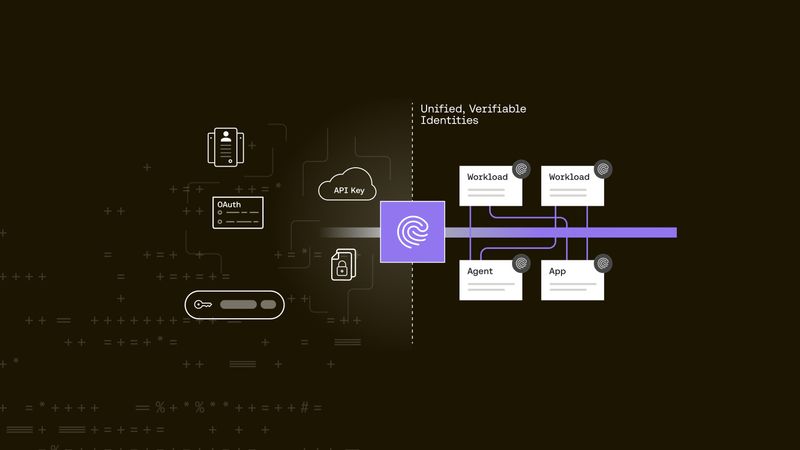
Zsolt Varga |SPIFFE Meets OAuth2: Current landspace for Secure Workload Identity in the Agentic AI Era
OAuth2 is evolving beyond human consent into a universal model for secure workload identity. Learn how SPIFFE and emerging OAuth2 standards form the foundation for safe, auditable agentic AI.SPIFFE -
 Balint Molnar |
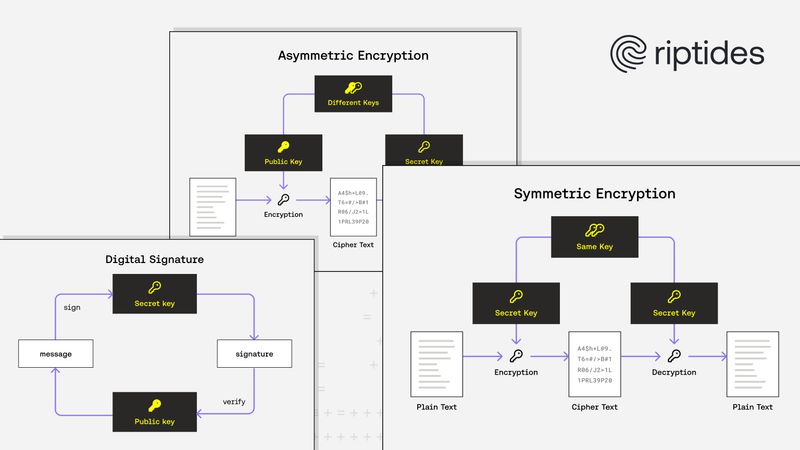
Balint Molnar |From Keys to Handshakes: How Cryptography Powers Riptides
In this blog post, we take a closer look at the cryptography that powers Riptides, the non-human identity fabric for workloads and AI agents. We break down the fundamentals of symmetric and asymmetric cryptography, explain how key exchange and digital signatures work, and compare RSA with Elliptic Curve Cryptography (ECC). To ground theory in practice, we share performance benchmarks demonstrating how ECC delivers faster handshakes and stronger security, making it the natural choice for Riptides.Security -
 Sebastian Toader |
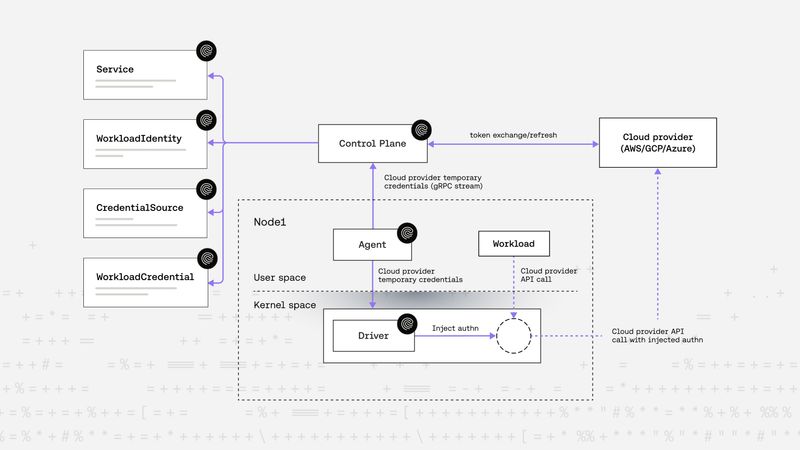
Sebastian Toader |On-the-Wire Credential Injection: Secretless AWS Bedrock Access example
Riptides brings secretless, on-the-wire credential injection to non-human clients. Instead of storing long-lived credentials, workloads receive short-lived credentials dynamically and transparently at runtime, they are injected and automatically refreshed. In this post, we demonstrate the approach using Amazon’s Product Agent Review app on Bedrock — but the same pattern applies across any cloud or service provider, reducing risk and simplifying non-human identity management.Federation -
 Nandor Kracser |
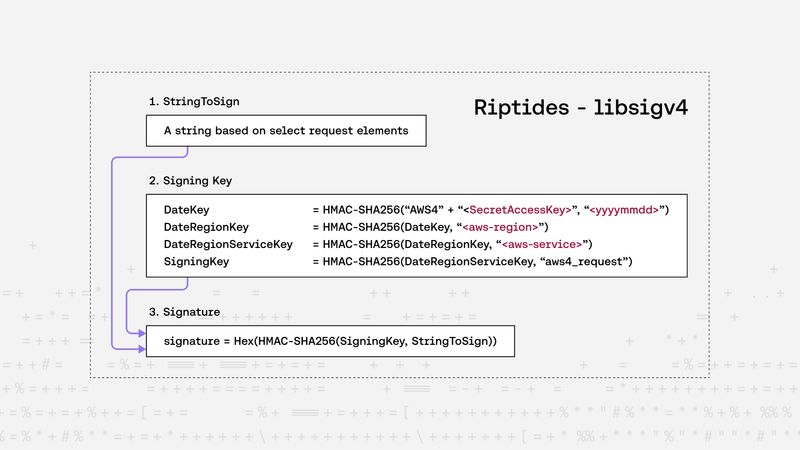
Nandor Kracser |Introducing libsigv4: AWS SigV4 Signatures in Portable C with Kernel Compatibility
We’ve released libsigv4, a lightweight and portable C implementation of AWS SigV4 signatures, built for kernel-based and embedded environments. It requires zero allocations, supports pluggable crypto backends, and depends on minimal system headers. Designed to integrate seamlessly with your own HTTP parsing, it’s an ideal fit for constrained platforms that need to communicate securely with AWS.Kernel -
 Nandor Kracser |
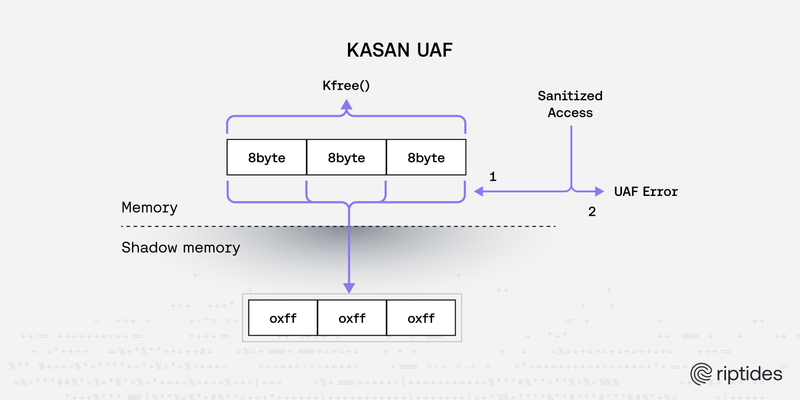
Nandor Kracser |Practical Linux Kernel Debugging: From pr_debug() to KASAN/KFENCE
Debugging kernel-space memory bugs is one of the most challenging tasks in systems programming. Fortunately, the Linux kernel comes with a rich toolbox of debugging features that can detect memory errors, race conditions, and invalid accesses - long before they cause a crash.Kernel -
 Sebastian Toader |
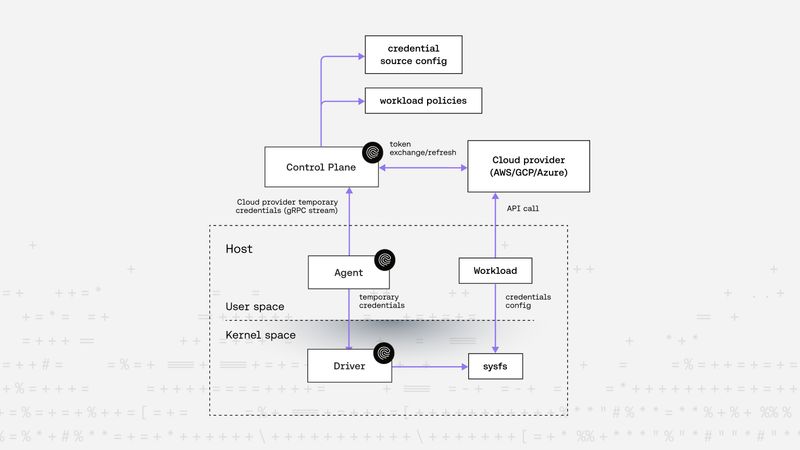
Sebastian Toader |Why Cloud-Native Federation Isn’t Enough for Non-Human Identities in AWS, GCP, and Azure
Cloud-native federation isn’t enough for secure, per-workload identity. AWS, GCP, and Azure support external IDPs, but today’s federation approaches fail to meet the needs of modern, large-scale non-human identities. They lack isolation, granularity, and still depend on brittle credential management. In this post, we explain why that's a problem and how Riptides solves it with zero secrets, SPIFFE-based identity, real-time credential issuance, and multicloud support. No code changes. No shared secrets. Just secure, automatic identity for every workload.Federation -
 Janos Matyas |
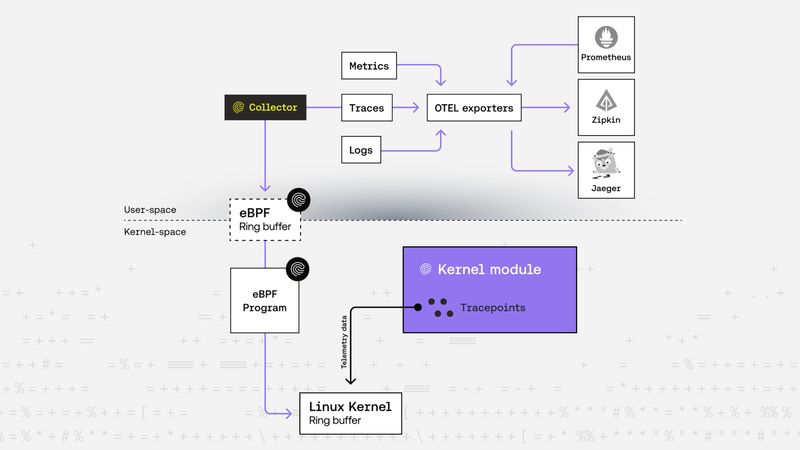
Janos Matyas |Securing Workloads with Kernel Telemetry and Metrics
Deep dive into how we turn low-level kernel signals to trust, using Linux kernel telemetry to secure non-human identities with real-time, behavioral context.Kernel -
 Zsolt Varga |
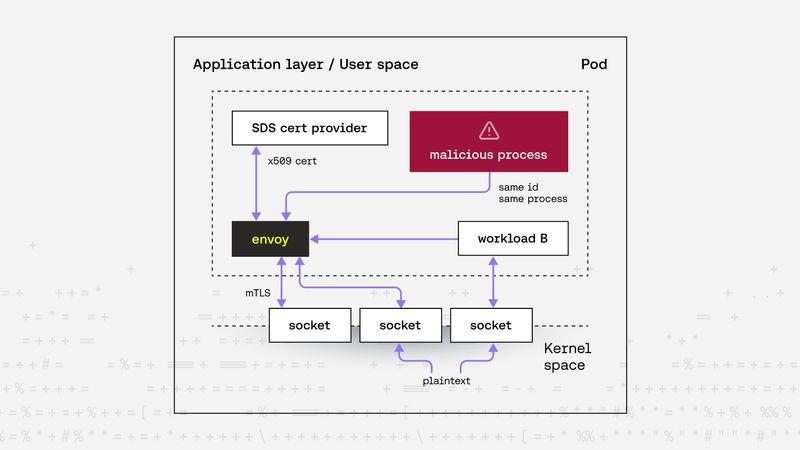
Zsolt Varga |The Hidden Risk in Service Mesh mTLS: When Your Sidecar Becomes a Trojan Horse
Even in a service mesh, mTLS can't protect you if any process can hijack your identity. See how attackers can exploit this gap and how to close it. We believe that real zero trust starts inside the kernel.Security -
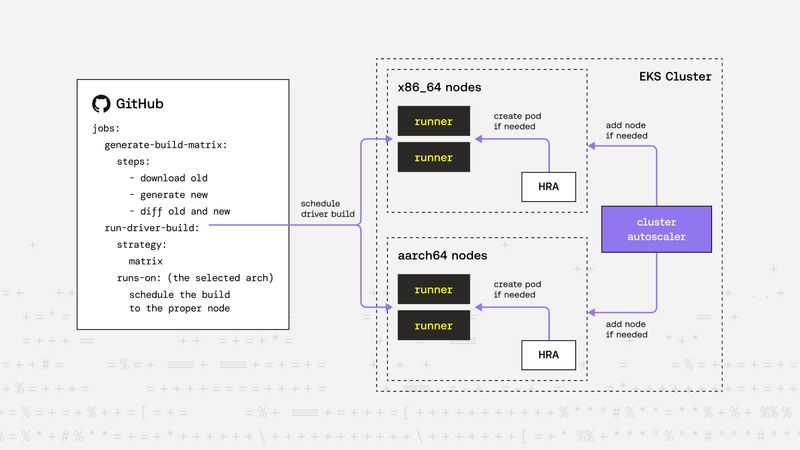 Peter Balogh |
Peter Balogh |Building Linux Driver at Scale: Our Automated Multi-Distro, Multi-Arch Build Pipeline
Managing driver builds for every major Linux distribution, kernel version, and architecture can be challengeing.Kernel -
 Janos Matyas |
Janos Matyas |SharePoint Under Siege: Lateral Movement Is Still Security’s Blind Spot
The ToolShell SharePoint 0-day shows how easily attackers move laterally once inside - even without escalated priviledges. Riptides stops this by enforcing per-process mTLS, posture checks, SPIFFE-based identity, and fine-grained policy controls, effectively blocking unauthorized communication and dramatically reducing the risk of lateral movement.Security -
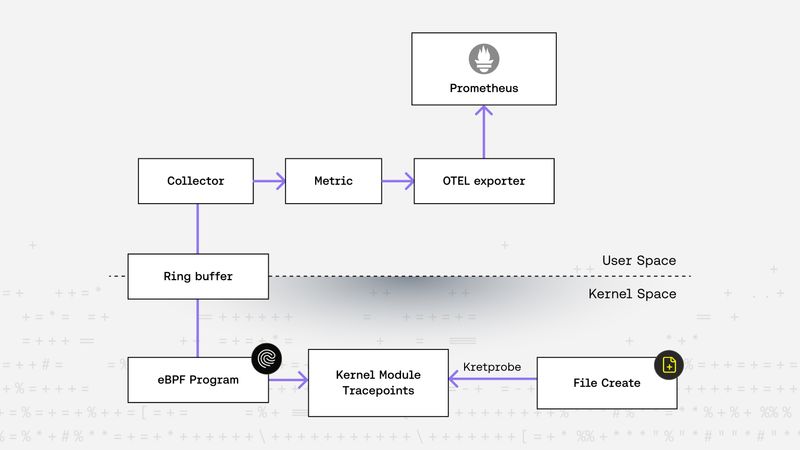 Zsolt Rappi, Balint Molnar |
Zsolt Rappi, Balint Molnar |From Tracepoints to Prometheus: The journey of a kernel event to observability.
This blog post illustrates how to build a complete end-to-end telemetry pipeline—from kernel space to Prometheus, using Linux tracepoints, eBPF, and OpenTelemetry (OTEL). We start with a custom kernel module that emits tracepoint events, then stream those events to user space using an eBPF ring buffer. Finally, we transform the raw events into structured Prometheus metrics with OTEL. The post includes a working open-source example and highlights practical debugging techniques using ftrace. This post builds on our ongoing Riptides telemetry series.Kernel -
 Janos Matyas |
Janos Matyas |The API Key Leaks Keep Coming
From x.AI to Docker Hub, API keys keep leaking. Static secrets are a ticking time bomb in today’s dynamic cloud world. Discover how kernel-native identity can eliminate this risk for good.Security -
 Janos Matyas |
Janos Matyas |Rethinking Workload Identity at the Kernel Level
Today’s workload identity systems are overengineered, inefficient, and fundamentally misplaced. Relying on userspace constructs like sidecars and proxies have worked at smaller scale — but they break under modern infrastructure demands. Worse, they detach identity from the actual workload, assigning it instead to a neighboring process. That’s not just a design flaw — it’s a security risk, opening the door to lateral movement, identity confusion, and broken trust boundaries. It's time to decouple security from proxies and issue identity at the source: the Linux kernel.Kernel -
 Sebastian Toader |
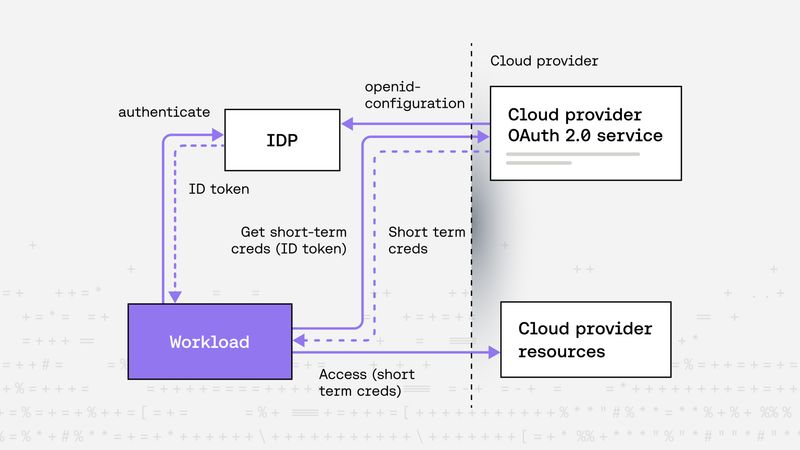
Sebastian Toader |Non-human identity federation with external IDPs: a guide for AWS, GCP, and Azure
Learn how to securely manage and federate non-human identities across AWS, GCP, and Azure using external OIDC-compliant identity providers. This post explains why traditional static credentials fall short, explores the benefits of federated ID tokens, and provides practical guidance on establishing trust and seamless multi-cloud access for modern cloud-native workloads.Federation -
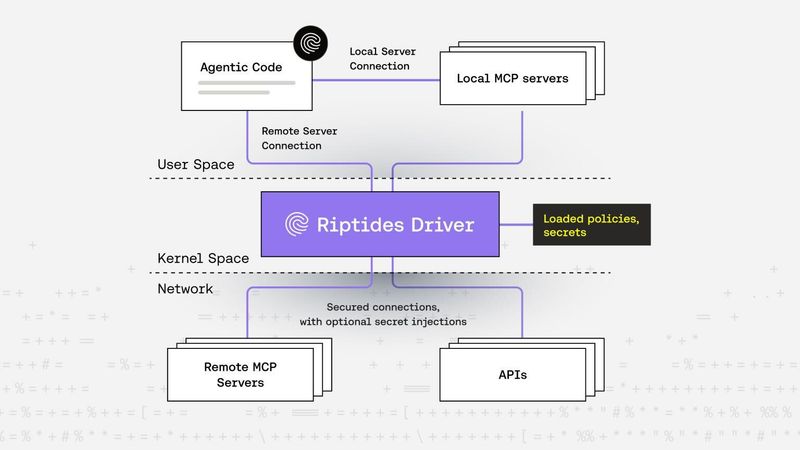 Zsolt Rappi |
Zsolt Rappi |Securing MCP Communication with Riptides
Agentic workload security is becoming increasingly important in today’s AI-driven world. This post explores how Riptides secures communication between agents and MCP servers using kernel-level mTLS, SPIFFE-based identity, and zero-trust policies, protecting against token leaks, impersonation, and other risks without requiring changes to application code.MCP -
 Zsolt Varga |
Zsolt Varga |X.509 Certificates in the Age of SPIFFE and Zero Trust
X.509 certificates remain a core building block for establishing trust between services, even in today’s dynamic, machine-driven environments. This post explains how X.509 works, where it falls short, and how modern frameworks like SPIFFE make it practical for non-human identity at scale.Security -
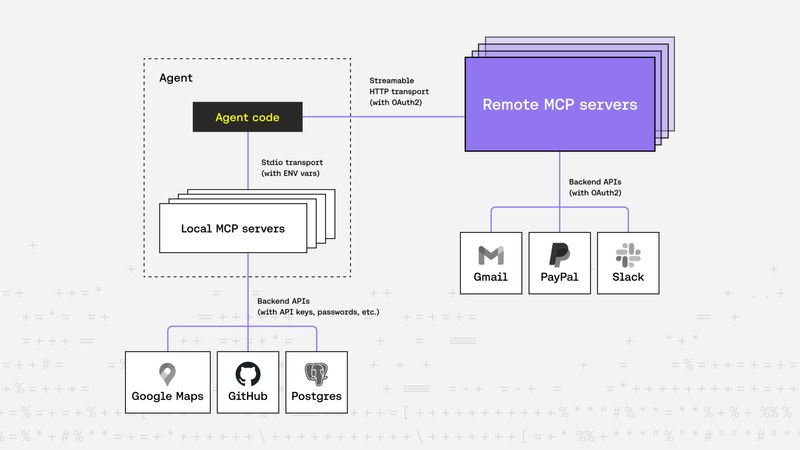 Zsolt Rappi |
Zsolt Rappi |MCP: A Quickstart Guide
MCP (Model Context Protocol)** is quickly becoming a foundational standard for enabling tool-augmented LLMs to interact with external systems. As the agentic ecosystem matures, so does the need for robust security, trust boundaries, and scalable identity. At Riptides, we’re focused on securing this new wave of agent driven interaction, especially where untrusted tools and dynamic decision making collide.MCP -
 Sebastian Toader |
Sebastian Toader |Linux kernel module telemetry: beyond the usual suspects
Why settle for surface-level metrics? At Riptides, we’re pushing kernel telemetry to the next-level high-performance, with enrichment and correlation alongside user space data.Telemetry -
 Janos Matyas |
Janos Matyas |Reflections from Identiverse: Why Security Needs Operational Efficiency
Insights from Identiverse 2025: why workload identity, SPIFFE, and in-kernel enforcement are key to securing modern infrastructure, without compromising operational efficiency.Conference -
 Nandor Kracser |
Nandor Kracser |Seamless Kernel-Based Non-Human Identity with kTLS and SPIFFE
At Riptides, we believe that the future of secure, scalable computing starts in the kernel. By moving critical identity management and mutual TLS (mTLS) operations into the Linux kernel, we eliminate the need for disparate authentication mechanisms in user space.Kernel -
 Janos Matyas |
Janos Matyas |Riptides is heading to Identiverse 2025!
We're excited to join the identity community this June to showcase how we’re rethinking non-human identity from the ground up.Identiverse -
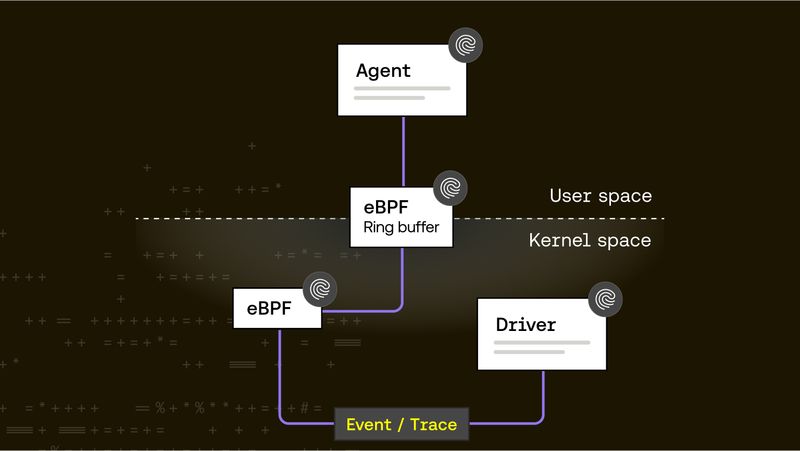 Balint Molnar |
Balint Molnar |From Tracepoints to Metrics: A journey from kernel to user-space
In our previous post, we’ve explored how to define tracepoints inside the kernel to gain deep visibility into system behavior. But tracing is only half the challenge—getting that data to user-space efficiently is the real test. In this post, we dive into the mechanics of streaming kernel events using eBPF and ring buffers, why we chose this path over character devices or netlink, and how we're building a high-performance telemetry pipeline that’s both modular and safe.Kernel -
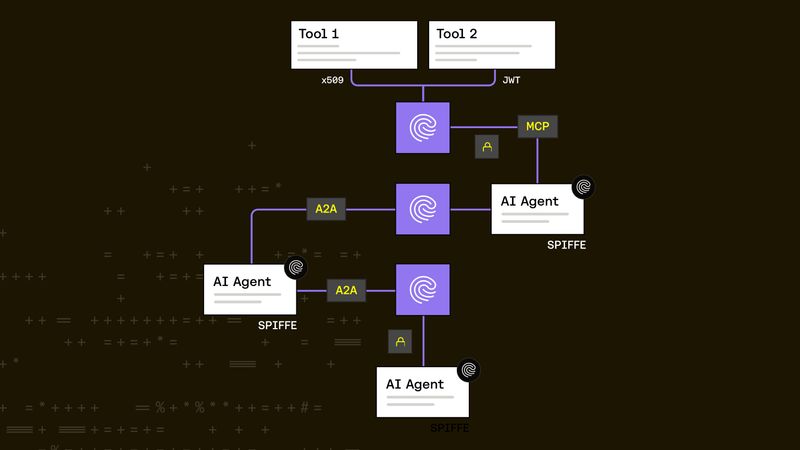 Janos Matyas |
Janos Matyas |Non-Human Identity Done Right: Why AI Agents Need SPIFFE and Riptides
AI agents are autonomous, but their security shouldn’t be an afterthought. This blog explores how SPIFFE provides strong identity for agents, why today’s authentication patterns fall short, and how Riptides delivers secure, automatic, kernel-level credentials that developers never need to manage.Identity -
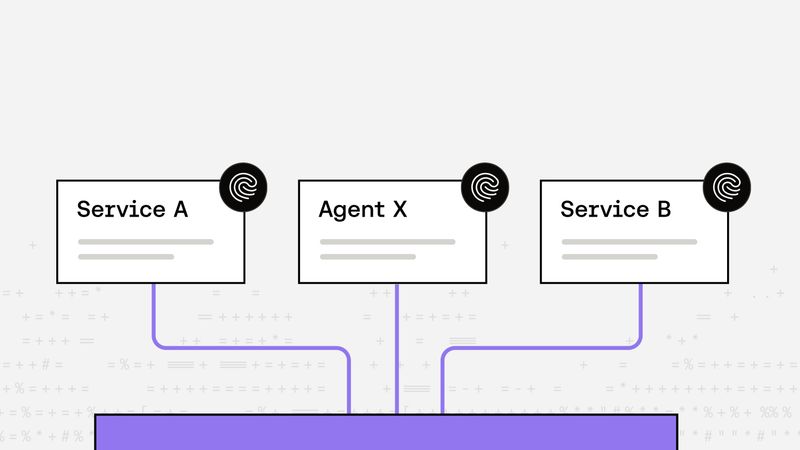 Zsolt Varga |
Zsolt Varga |The Critical Role of Unique Workload Identity in Modern Infrastructure
As modern infrastructure becomes more dynamic and distributed, securing service-to-service communication requires moving beyond static credentials to cryptographically verifiable workload identities using standards like SPIFFE and x509 certificates.Identity -
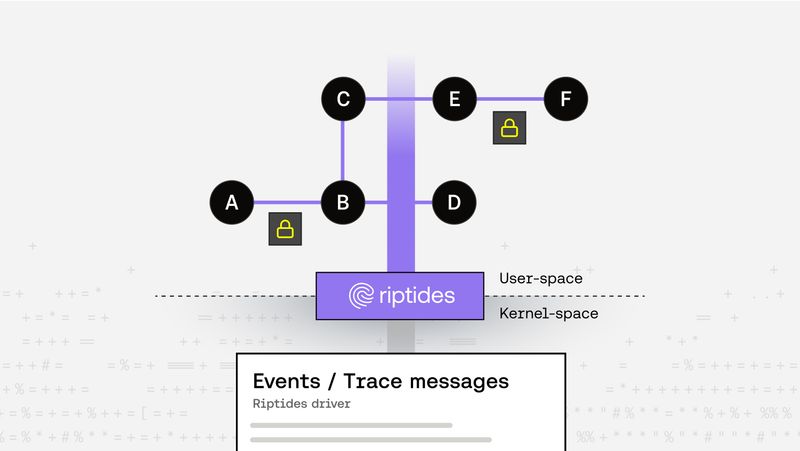 Balint Molnar |
Balint Molnar |From Breakpoints to Tracepoints: An Introduction to Linux Kernel Tracing
We can all agree that in today’s modern infrastructure, the significance of non-human identities has grown dramatically. Automatically provisioning identities for services has become a critical responsibility for security and infrastructure teams.Kernel -
 Marton Sereg |
Marton Sereg |The Riptides Vision: Identity-First Infrastructure
Identity -
 Janos Matyas |
Janos Matyas |Introduction to SPIFFE: Secure Identity for Workloads
The Riptides Platform is a comprehensive solution for securing workload-to-workload communication, built on a foundation of identity. It provides a universal and transparent non-human identity solution that secures every connection between workloads and services. One of the pillars of the Riptides’ identity platform is SPIFFE, the Secure Production Identity Framework for Everyone.Identity -
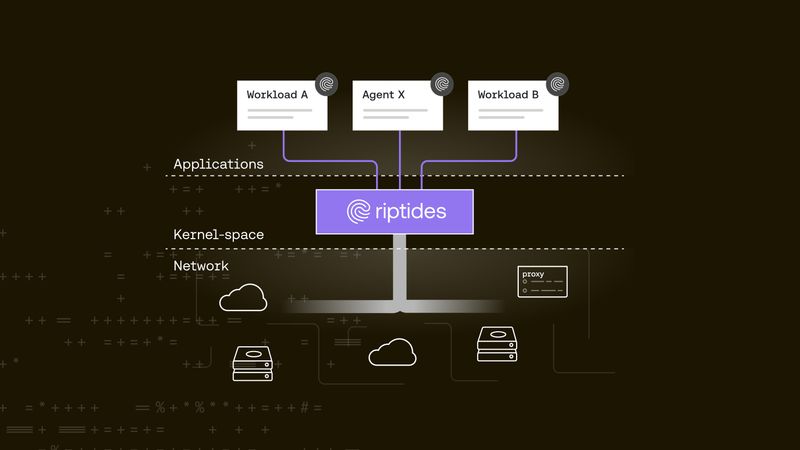 Nandor Kracser |
Nandor Kracser |Riptides: Kernel-Level Identity and Security Reinvented
Reinventing Non-Human Identities with Kernel TLS: How Riptides is Shaping the Future of Secure, Dynamic ApplicationsKernel