AI remains the headline topic of our industry, but the consensus is becoming clear: AI agents are workloads. They require identities, credentials, and policies just like any other component in a distributed system. What makes them different is not that they need identity, but how they use it: demanding fine-grained authorization controls that reflect their dynamic behavior, decision boundaries, and delegated autonomy. Treating AI as a first-class workload identity subject unlocks consistent governance, observability, and trust across both human and machine interactions. At the same time, SPIFFE has emerged as the industry standard for workload identity, a standard we’ve believed in from the very beginning, and one of the core principles around which Riptides was built. SPIFFE provides a consistent and secure way to issue, rotate, and verify credentials for workloads, services, and now AI agents at scale. Yet, until recently, one crucial piece of the puzzle was missing, the connective layer that could bring SPIFFE-based identity into the agentic world.
MCP: The Emerging Fabric of Agentic Communication
The Model Context Protocol (MCP) is rapidly becoming the backbone for secure, structured communication between AI agents and the tools or data providers they depend on. It defines a common language for agents to discover, describe, and interact with capabilities hosted across a distributed network of MCP servers. As MCP evolves into the connective tissue of agentic ecosystems, it inherits a critical challenge: how to use OAuth securely while supporting massive numbers of dynamically registered, short-lived agents.
In earlier posts, we explored how Riptides secures MCP communication using workload-based identity and kernel-enforced controls, and how SPIFFE and OAuth2 together can form the foundation for workload authentication in OAuth-based systems. In this post, we take that vision further and discuss how we have implemented the emerging OAuth RFC drafts for SPIFFE-backed OAuth and building a demo MCP application that showcases this integration in a Riptides environment.
This fusion unlocks a new model of self-registering, self-authenticating workloads, particularly AI agents, forming a key building block for scalable, autonomous, and verifiable agentic ecosystems.
The Identity Problem in Agentic AI
Agentic AI systems rely on dynamic, autonomous workloads that come and go as tasks evolve. An agent might spawn new processes to handle context expansion, fetch data from a remote MCP server, or delegate work to a specialized sub-agent. In every case, the system must establish mutual trust between participants and it must do so automatically, at scale.
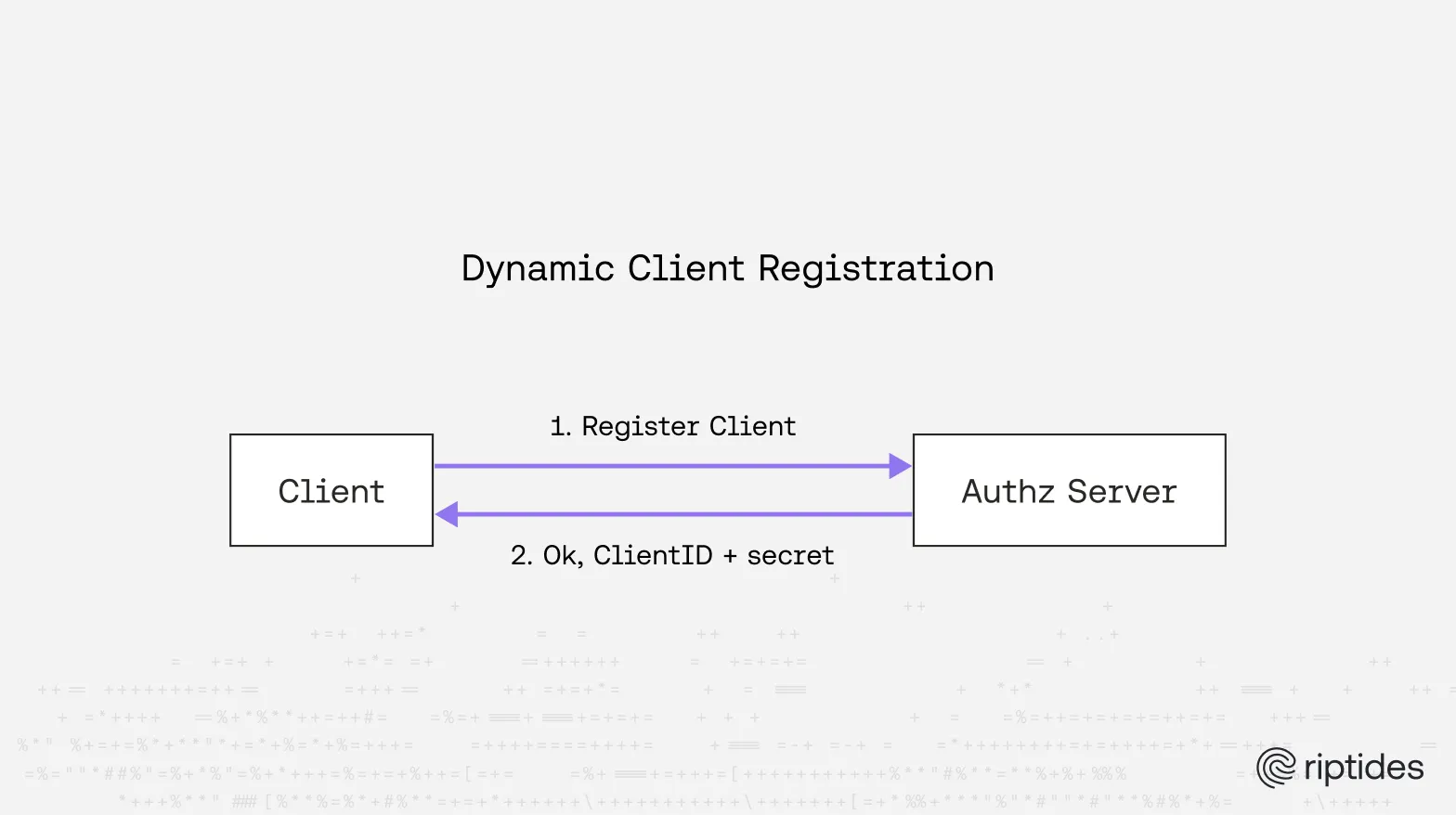
Traditionally, workload authentication in OAuth has been secret-based: each client is registered at the authorization server with a *client ID and secret. This model breaks down in dynamic environments where workloads are ephemeral and scale on demand, since credentials must be provisioned, stored, and rotated securely. In an agentic ecosystem where hundreds or thousands of short-lived agents and tool instances may interact fluidly, this approach is simply not sustainable.
Static credentials also violate core zero-trust principles: identity should be ephemeral, verifiable, and bound to the workload itself, not tied to configuration files or long-lived and shared secrets.
SPIFFE and OAuth
SPIFFE (Secure Production Identity Framework for Everyone) defines a standard for issuing and verifying cryptographically strong identities for workloads. Each workload receives a SPIFFE Verifiable Identity Document (SVID), an X.509 certificate or JWT, that attests to its identity within a trust domain (for example, spiffe://riptides.io/workload/mcp-server).
These credentials are short-lived, automatically rotated, and anchored in strong cryptographic trust roots managed by an issuer. They establish who a workload is, verifiably and dynamically, without relying on pre-shared secrets.
OAuth, by contrast, defines how workloads obtain access tokens for APIs, but it traditionally assumes that clients are pre-registered with a client ID and secret at the authorization server. That static model works for stable applications but breaks down in systems where workloads are ephemeral or autonomously created, such as agentic AI.
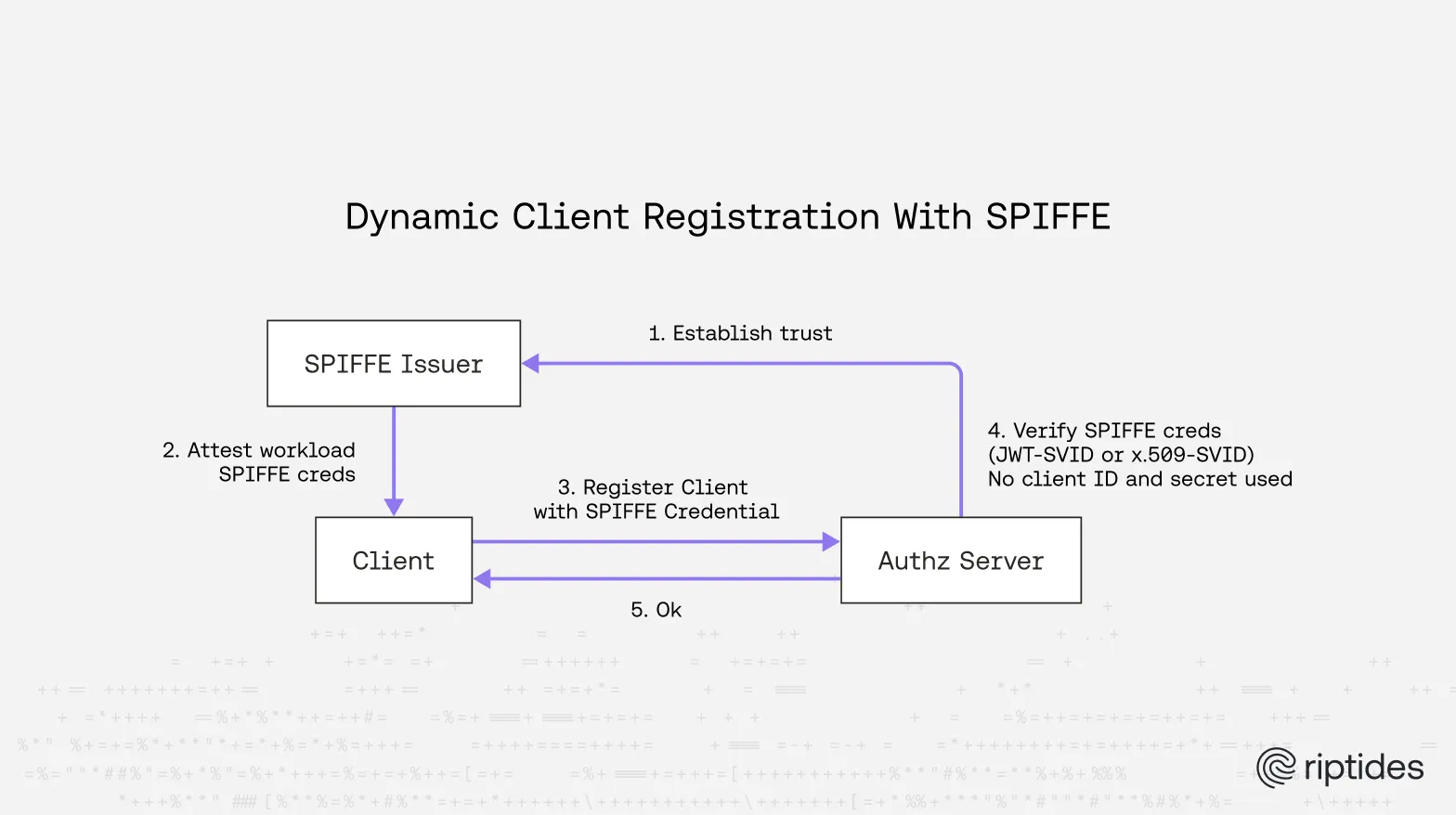
By treating SPIFFE credentials as software statements within OAuth, we can bridge this gap. A workload can prove its identity, self-register as an OAuth client, and immediately perform standard OAuth flows, all without manual configuration or stored secrets.
Here’s how Dynamic Client Registration with SPIFFE would look like:
SPIFFE-Backed OAuth in Riptides: Implementing Emerging RFCs
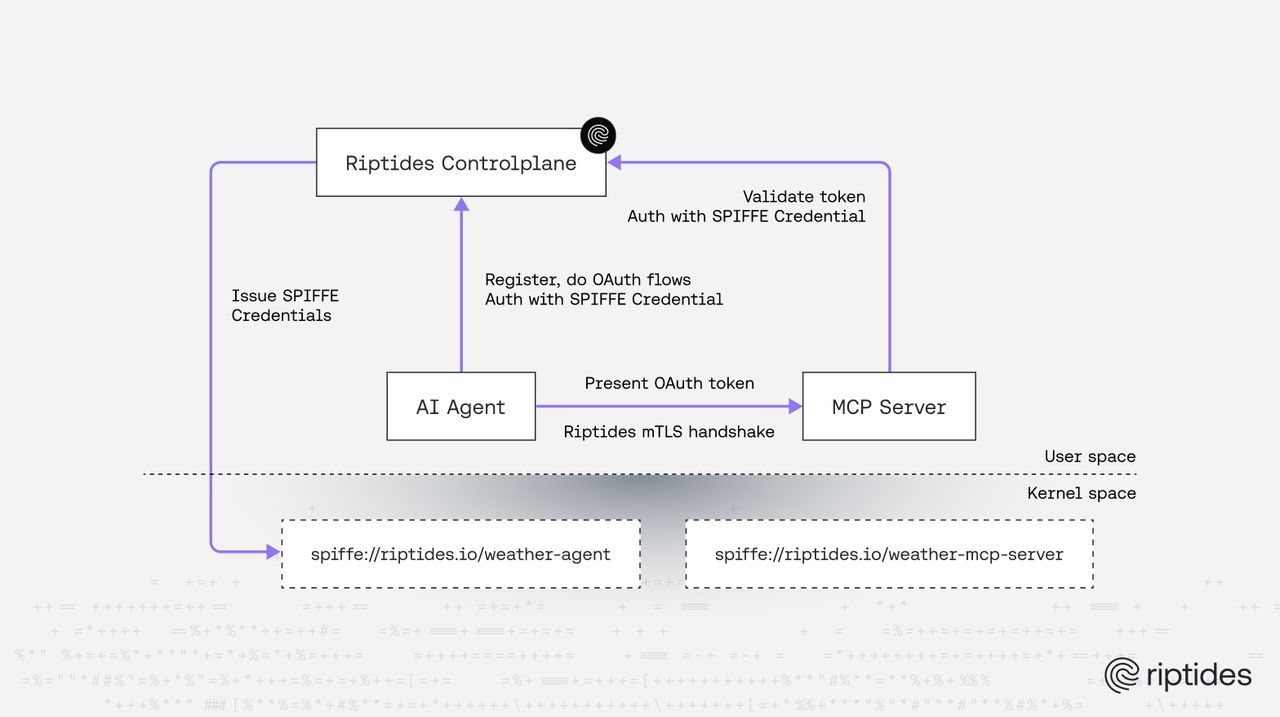
The Riptides Controlplane functions as both a SPIFFE issuer and an OAuth/OIDC authorization server within the Riptides ecosystem. This architecture made it straightforward to layer a SPIFFE-based authentication system in front of the existing OIDC server. Riptides-managed workloads, which automatically receive SPIFFE credentials at the kernel level, can seamlessly authenticate with the Controlplane’s OAuth endpoints and obtain tokens to access protected resources, such as remote MCP servers.
In our demo setup, both the MCP client and MCP server run as Riptides-managed workloads. Each receives a valid SPIFFE identity issued by the Controlplane and injected at the kernel level. When communication is required, for instance, when an MCP client calls a remote MCP server, the workloads use their SPIFFE credentials to self-register and authenticate via OAuth, without any manual configuration.
At a high level, the lifecycle works as follows:
- Obtain SPIFFE credentials: Workloads receive SVIDs from the Controlplane, automatically injected into traffic at the kernel level, without code changes required.
- Present credentials: The agent uses its SVID as the proof element in OAuth flows (client registration, token request, etc.).
- Validate credentials: The OAuth server verifies the SVID against the trusted issuer.
- Token introspection: The MCP server validates tokens at the Controlplane’s introspection endpoint, authenticating itself via its own SVID.
This approach transforms OAuth into a dynamic, identity-aware trust fabric, naturally aligned with MCP’s model of tool discovery, invocation, and secure agent-to-agent communication.
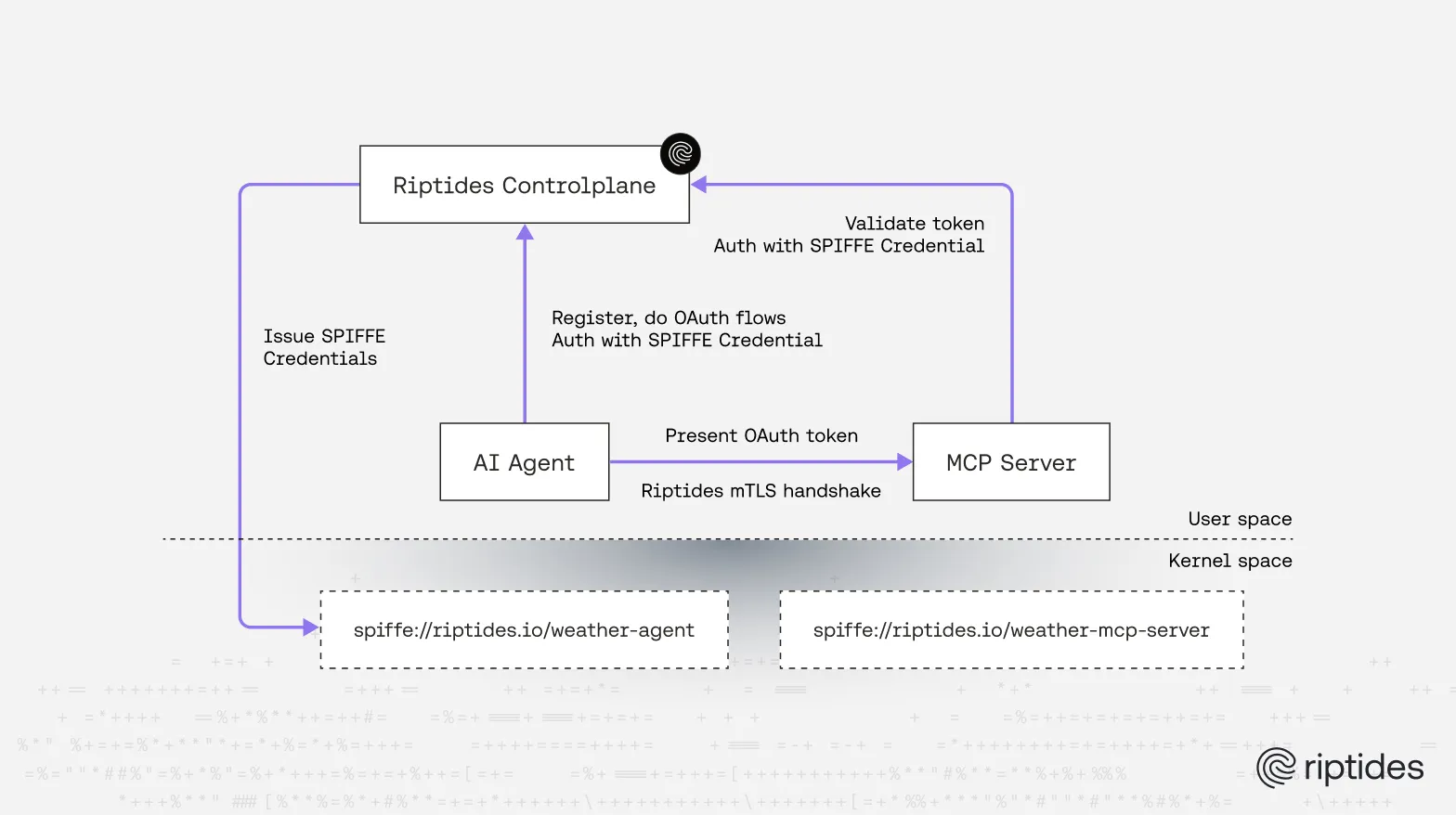
The two workloads, the agent and the MCP server, are defined in Riptides using the following WorkloadIdentity specifications:
apiVersion: core.riptides.io/v1alpha1
kind: WorkloadIdentity
metadata:
name: weather-mcp-server
spec:
scope:
agentGroup:
id: spiffe-mcp-demo-agent-group
selectors:
- process:uid: [501, 1001]
process:name: [python]
process:cmdline: python mcp_server.py
workloadID: weather-mcp-server
---
apiVersion: core.riptides.io/v1alpha1
kind: WorkloadIdentity
metadata:
name: weather-agent
spec:
scope:
agentGroup:
id: spiffe-mcp-demo-agent-group
selectors:
- process:uid: [501, 1001]
process:name: [python]
process:cmdline: python mcp_client.py
workloadID: weather-agentWhy SPIFFE-Backed OAuth Matters for MCP and Agentic AI
With SPIFFE-backed OAuth in Riptides, workloads gain several operational and security advantages:
- No manual setup: Workloads self-register automatically using identity-based proof.
- No code changes: Identities are issued automatically and injected into traffic at the kernel level.
- No secrets at rest: Authentication relies on short-lived, ephemeral certificates instead of static client secrets.
- Cross-domain scalability: Trust is based on cryptographic identity rather than configuration.
- Automatic rotation: SPIFFE’s short-lived credentials ensure continuous renewal and revocation.
- Traceable accountability: Every token and registration event is tied to a verifiable workload identity, which can be audited and correlated with runtime telemetry.
- Reduced attack surface: Removing client secrets and configuration files minimizes the risk of credential leakage.
- Consistent policy enforcement: Identity and authorization policies are applied uniformly at the Controlplane and enforced at the workload level.
For MCP in particular, this enables remote servers to accept connections from legitimate agents on demand, enforce policies based on concrete workload identities, and avoid distributing sensitive credentials at scale. Agents can discover and invoke tools seamlessly, while operators maintain full governance, traceability, and auditability across the system.
Together, these benefits enable organizations to scale agentic AI systems securely, maintaining both operational efficiency and a strong security posture while preserving full auditability and governance.
Operational Challenges and Practical Considerations
While this model is powerful, several operational considerations must be addressed:
- Token binding and proof-of-possession (PoP): Tokens should be cryptographically bound to the presenting identity to prevent replay attacks.
- Client lifecycle management: Even with dynamic registration, workloads require proper lifecycle management, including deregistration, credential revocation, and policy updates, all of which must be auditable.
- Trust-domain governance: Operators need to define and enforce which SPIFFE issuers are trusted, along with the constraints that apply across trust boundaries.
Addressing these considerations ensures that dynamic, SPIFFE-backed OAuth systems remain secure, auditable, and manageable at scale.
Conclusion: Dynamic Trust for Agentic AI
Treating SPIFFE credentials as software statements for OAuth eliminates manual configuration, removes static secrets, and enables secure, automated interactions between agents and tools. For MCP and the broader agentic AI ecosystem, this approach is foundational. It transforms OAuth from a friction point into a dynamic, identity-aware trust fabric, turning identity itself into the API that governs who can do what, when, and why, all in a scalable, auditable, and automated manner.
At Riptides, we envision a world where all non-human workloads, from ephemeral AI agents to distributed services, can authenticate, authorize, and interact securely without manual intervention. By combining kernel-enforced SPIFFE identities with dynamic OAuth flows, we aim to make trust, governance, and policy enforcement invisible but verifiable, so teams can focus on building capabilities rather than managing credentials. This is the foundation for truly autonomous, secure, and auditable agentic systems at scale, where identity drives both innovation and safety.
If you enjoyed this post, follow us on LinkedIn and X for more updates. If you'd like to see Riptides in action, get in touch with us for a demo.